
By Josh Stearns
On the eve of Super Tuesday, a New York Times article made the rounds on social media reporting that Massachusetts Senator Elizabeth Warren had endorsed Sen. Bernie Sanders for president. The only problem: It was fake.
The New York Times released a statement and others debunked the fake on Tuesday, as people were headed to the polls, but by that point the fake article “had been viewed more than 50,000 times, with 15,000 shares on Facebook,” the Times reported.
This is just the another in a long line of fake news reports which have swept through social media in recent years. Last year Twitter’s share price spiked after a fake Bloomberg article claimed that Google was considering buying the social media platform. In 2012, Wikileaks created a fake New York Times op-ed from then-Times-editor Bill Keller defending Wikileaks in what appeared to be a change of position from his earlier statements about the group. The fake was so convincing that even New York Times journalists were sharing it on Twitter.
More recently, a fake Daily Mail article claiming Syrian refugees were “offered new homes on an occupied army base” in the UK was picked up by a number of far-right and anti-refugee Facebook pages, spreading the hoax further. Both the fake Daily Mail and New York Times articles were made using CloneZone, which allows users to make fake articles in the style of many real publications.
This kind of hoax isn’t limited to the web though. Just a few weeks ago a pro-Palestinian group handed out fake versions of the New York Times to highlight what it believes is the Time’s bias against Palestinians. In 2008 the Yes Men distributed thousands of copies of a 14-page fake New York Times all over New York City. The paper declared the end of the Iraq war on the front page.
Online it is increasingly simple for activists and pranksters to spoof the look and feel of a major news website and these fakes can have real impacts from Wall Street to the voting booth. However, in each of these past cases there has been some clear giveaways that are instructive for anyone who wants to spot fakes in the future.
Here are five ways to make sure you don’t get duped by a fake website.
URL shorteners on social media often hide a website’s actual domain address which makes it all the more important to click through to a full page. Even the previews that appear on Facebook and Twitter can be made to look convincingly like actual news articles and brands. But sometimes even after you click through to the page the URL can be customized to fool people.
The URL for the fake Wikileaks op-ed from Bill Keller was the first clue that something was amiss. The URL was “opinion-nytimes.com,” when in fact the real opinion section of the Times is located at “nytimes.com/pages/opinion.” The practice of tweaking URLs with words like this is common in phishing attacks designed to steal personal information. (The Freedom of the Press Foundation has a guide to spotting phishing attempts.)
In the case of the fake Bloomberg article about a possible Twitter sale, the piece was housed at “bloomberg.market,” which is not a URL used by Bloomberg. With the proliferation of new top level domains (.limo, .news, etc…) it is all the more important to double check the URL before sharing any web page.
No matter how well a person or organization try to mimic the style and design of a news organization there are often small but meaningful mistakes that can raise red flags.
In its coverage of the Bloomberg fake the New York Times wrote “Close scrutiny, however, flagged a number of questionable elements in the piece. The name of Twitter’s former chief, Dick Costolo, was misspelled. The grammar seemed off. The byline was Stephen Morris, who covers British banks.” And at the time Bloomberg reporters pointed out “the article was rife with violations of the news organization’s often-rigid writing style commandments.”
In the case of the fake Keller op-ed, things were a little trickier because Wikileaks actually drew from real quotes from a recent interview Keller had done with Mathew Ingram. However, Glenn Greenwald, writing in a post-mortem about the fake noted that it included “extraordinary claims” about the government’s attacks on Wikileaks that he hadn’t heard before. Checking on those claims led Greenwald to spot the fake (and an accompanying fake PayPal blog post). Ernie Smith of the ShortFormBlog put together a nice side-by-side comparison of the fake Keller piece with a real Keller piece.
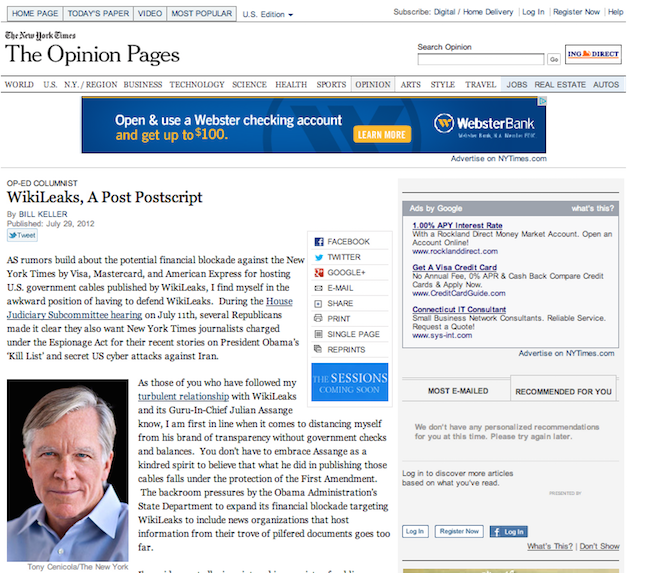
The fake Bill Keller opinion piece, created by WikiLeaks
Who first shares something can tell you a lot about the origins and the legitimacy of a webpage. Use Twitter’s advanced search, Facebook’s graph search or a tool like Storyful’s Multisearch plug-in to search for a link, then sort results chronologically to find the earliest occurrence on a particular platform, or limit the search to a particular time frame.
Security researcher Chris Soghoian pointed out that some of the first accounts to tweet the fake Bill Keller Wikileaks article were Wikileaks and Anonymous. Others pointed to an account called @Block_NYTimes which shared the link early on. All of these things should have been red flags. However, you also have to beware fake Twitter accounts.
In this case @NYTKeller, featuring Bill Keller’s photo and bio, tweeted the article but Bill Keller’s actual Twitter account was actually @billkeller2014. (Related: Find out how to spot hoax accounts and fake eyewitnesses on Twitter.)
WhoIs data can reveal details about who registered the domain name, their address and even their contact information. You can do a WhoIs search from the ICANN site and here are some tips on WhoIs searches for journalists.
But sometimes you have to dig deep to find what you are looking for. Back in 2012 when the fake Keller op-ed came out BetaBeat wrote: “Whoever registered it was also incredibly detail-oriented: the WhoIs information for the fake site notes the registrant as ‘Ellen Herb,’ the same person who is listed as the registrant for the real nytimes.com URL. Sneaky!”
BetaBeat kept digging though, and discovered that “opinion-nytimes.com possesses the same NIC handle as ‘blocknytimes.org,’ another site registered on Gandi, a French domain hoster.” The fake PayPal blog post was also linked to that NIC handle. Finally, opinion-nytimes.com was registered in March, the same month the @Block_NYTimes Twitter account was started. Since the site didn’t go live until July it is clear Wikileaks had been planning this for some time.
Diving into the source code of a page is not for the faint of heart. You usually have to know what you are looking for and what you are looking at, but sometimes there are surprises hiding in plain view (from secret messages to job postings).
On his Online Journalism blog, Paul Bradshaw suggests that “Occasionally hoaxers intentionally leave clues here, but you can also find other clues such as the author, date, location, and technologies used.”
In looking into the fake Keller op-ed, Twitter user @shawnmer noticed that the image file used for the Facebook “Like” button was actually an image file from Olympic snowboarder Mark McMorris’ personal website. (The @shawnmer Twitter account is closed, but the original Tweet is archived in this Storify.)
The authors of the Data Journalism Handbook argue that “Even if they’re just copyright notices or mentions of the author’s names, these can often give important clues about the creation and purpose of the page.” Here is a quick guide to how to view the source code of a website in each browser and what to look for.
In most cases you won’t need to go mining the HTML code to find out if a piece is a fake, there are enough other signs. The Warren/Sanders article was created using a site called Clone Zone. The other Clone Zone articles I looked at all included a small crawler at the bottom of the page pointing out that these are spoofed pages. However, my guess is most people saw the headline, framed in the familiar New York Times web design and shared it before ever glancing down at the bottom of the page.
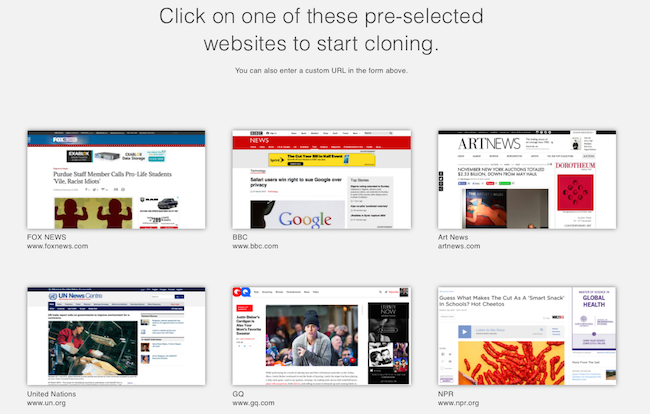
In 2012 Craig Silverman described these sorts of fake news websites as “a hoax designed not just to fool, but to spread”. The New York Times responded to the fake quickly, releasing a statement about the article and it says that from here on out the nytimes.com URL has been blocked from future cloning. However, I found many other New York Times clones and hoaxes still posted on Clone Zone’s website – many with thousands of views. Clone Zone also offers featured templates for people to create fake BBC, NPR and even United Nation’s websites.
This isn’t a problem that is going to go away, so newsrooms, journalists and news consumers need to more skeptical and careful before sharing. Finding ways to engage readers and encourage skepticism without letting these kinds of hoaxes erode trust is going to be an ongoing negotiation.
(In 2012 I wrote a brief guide on spotting hoax websites. This post is based on some of that earlier work, but expanded and updated with new information and resources)
Update: This article has been updated to include a reference to the fake Daily Mail article.